Build and Secure Networks in Google Cloud: Challenge Lab
The challenge contains 6 required tasks:
- Remove the overly permissive rules
- Start the bastion host instance
- Create a firewall rule that allows SSH (tcp/22) from the IAP service and add a network tag on
bastion - Create a firewall rule that allows traffic on HTTP (tcp/80) to any address and add a network tag on
juice-shop - Create a firewall rule that allows traffic on SSH (tcp/22) from
acme-mgmt-subnetnetwork address and add a network tag onjuice-shop - SSH to bastion host via IAP and
juice-shopviabastion
Let's do it one by one :))
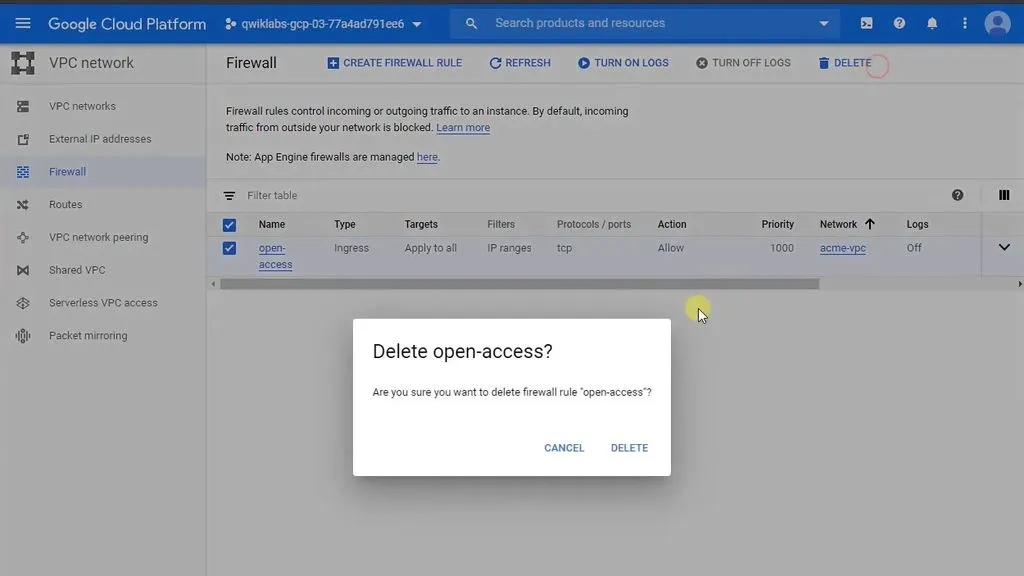
1. Remove the overly permissive rules
This task is very simple. You only need to the open-access firewall rules.
- In the Cloud Console, navigate to Menu > VPC Network > Firewall
- Check the box next to the rule named
open-access. - Click on DELETE to remove it.
2. Start the bastion host instance
- In the Cloud Console, navigate to Menu > Compute Engine > VM instances
- Check the box next to the instance named
bastion. - Click on Start to run the instance.
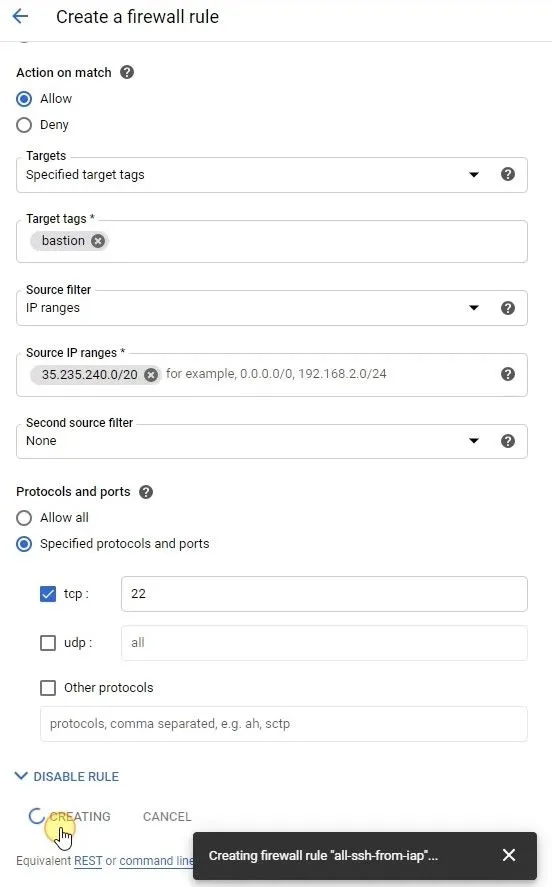
3. Create a firewall rule that allows SSH (tcp/22) from the IAP service and add network tag on bastion
Add network tag on bastion
- On the VM instances page, click on the name of the bastion instance.
- Click EDIT on the details page.
- Add
bastionto the Network tags field. - Scroll to the button of the page and click Save.
Create firewall rule to allow SSH from the IAP service
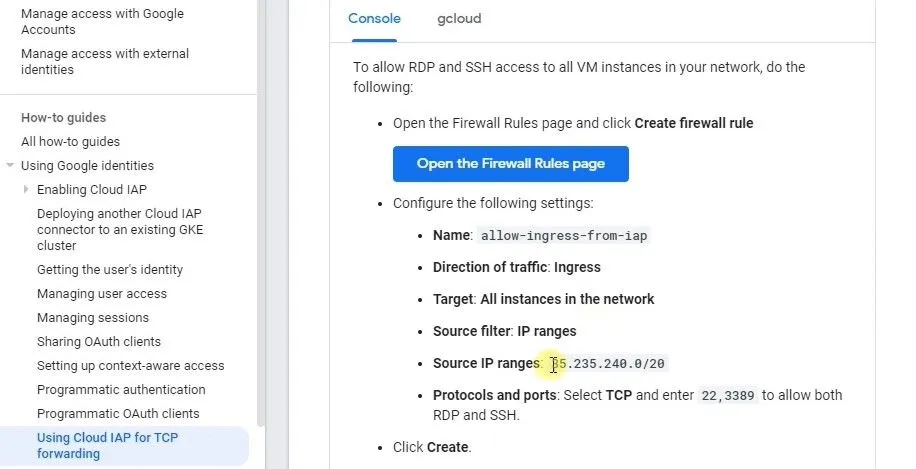
Read Using IAP for TCP forwarding in the Google Cloud Documentation before you create the firewall rule.
- Go back to the Firewall Rules page, and click Create firewall rule.
Configure the following settings:
Field Value Name e.g. allow-ssh-from-iapDirection of traffic Ingress Targets Specified target tags Target tags bastionSource IP ranges 35.235.240.0/20Protocols and ports Select TCP and enter 22to allow SSH
4. Create a firewall rule that allows traffic on HTTP (tcp/80) to any address and add network tag on juice-shop
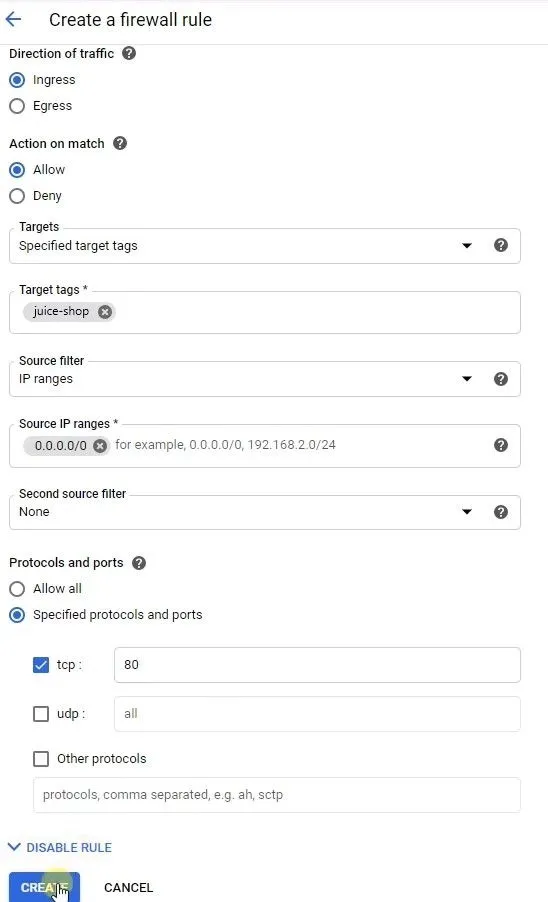
Create firewall rule to allow HTTP traffic to juice-shop
- On the Firewall Rules page, and click Create firewall rule.
Configure the following settings:
Field Value Name e.g. allow-http-ingressDirection of traffic Ingress Targets Specified target tags Target tags juice-shopSource IP ranges 0.0.0.0/0Protocols and ports Select TCP and enter 80to allow HTTP
Add network tag on juice-shop
- On the VM instances page, click on the name of the juice-shop instance.
- Click EDIT on the details page.
- Add
juice-shopto the Network tags field. - Scroll to the button of the page and click Save.
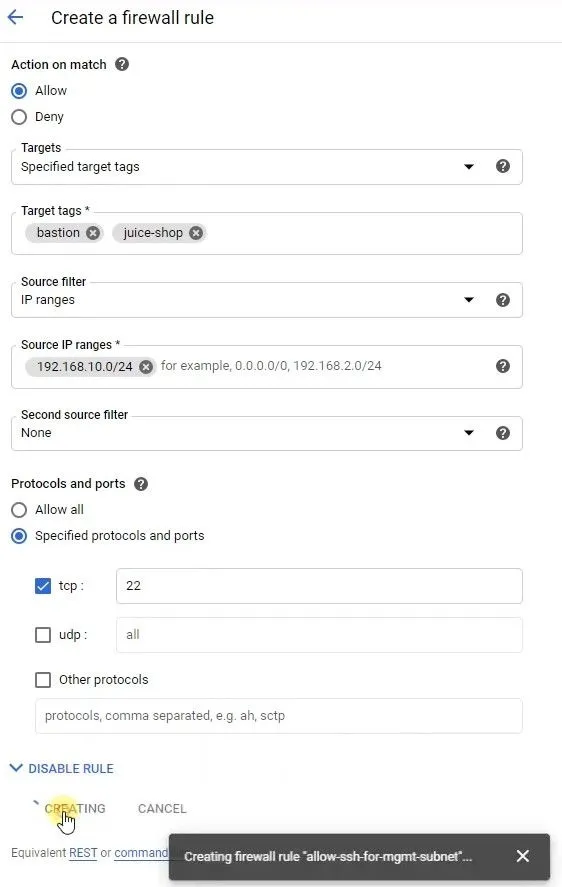
5. Create a firewall rule that allows traffic on SSH (tcp/22) from acme-mgmt-subnet network address and add network tag on juice-shop
- Navigate to VPC network > VPC networks.
- Copy the IP address range of the
acme-mgmt-subnet. - Go back to the Firewall Rules page, and click Create firewall rule.
Configure the following settings:
Field Value Name e.g. allow-ssh-from-mgmt-subnetDirection of traffic Ingress Targets Specified target tags Target tags bastionandjuice-shopSource IP ranges IP address range of your aceme-mgmt-subnet Protocols and ports Select TCP and enter 22to allow SSH
6. SSH to bastion host via IAP and juice-shop via bastion
After configuring the firewall rules, try to verify the environment via the bastion.
- Navigate to Compute Engine > VM instances.
- Copy the Internal IP of the juice-shop instance.
- Click on the SSH button in the row of the bastion instance.
In the SSH console, access the juice-shop from the bastion using the following command:
ssh <internal-IP-of-juice-shop>(Remember to REPLACE
<internal-IP-of-juice-shop>with the copied IP address)
Congratulations! You completed this challenge lab.